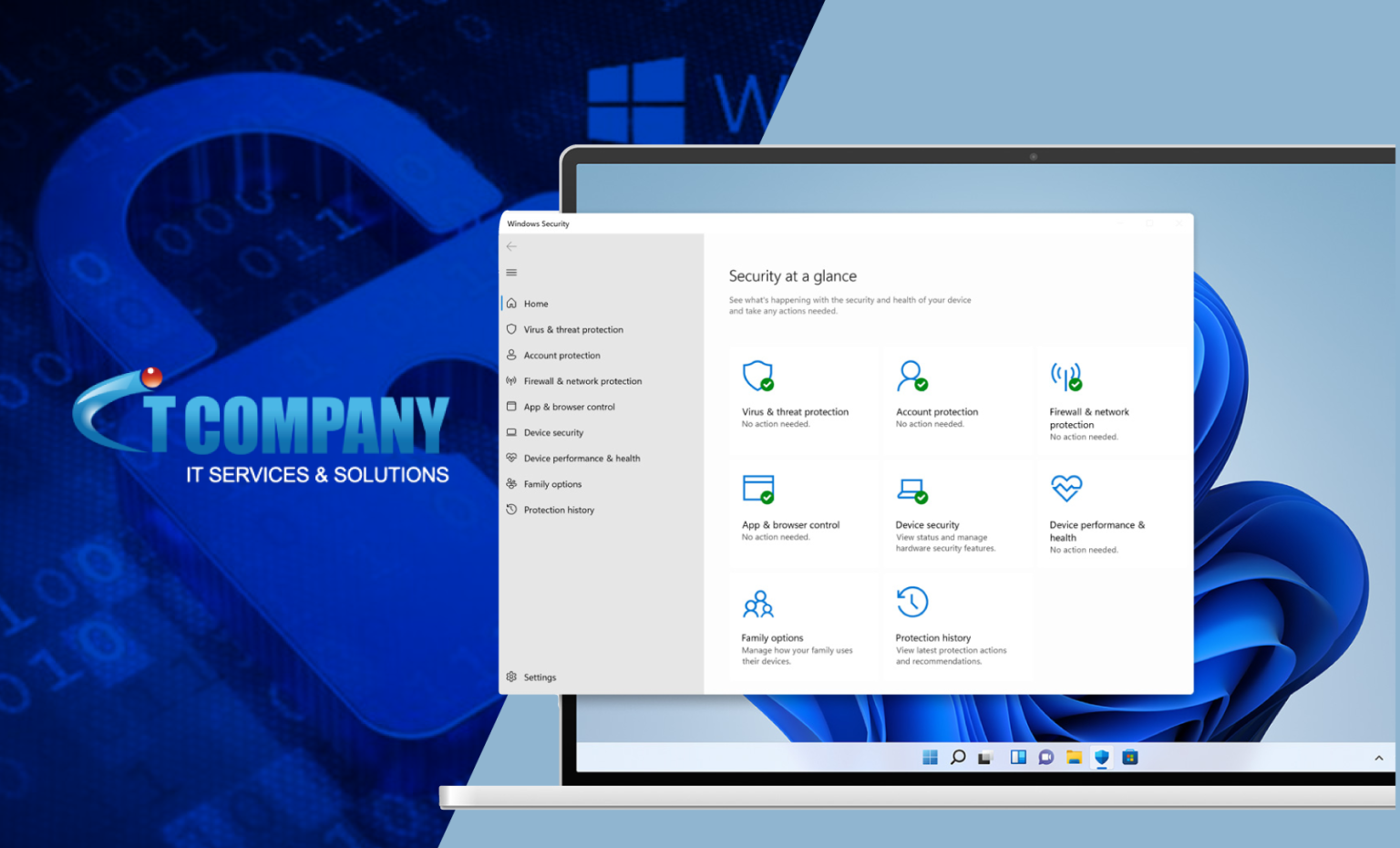
What if phony applications aren’t identified?
A significant issue in Windows-powered data centers and applications that Microsoft resolved in mid-2022 remains unpatched across virtually all susceptible endpoints. It has placed countless people in danger of malware and ransomware assaults.
The cybersecurity website experts developed a proof-of-concept (PoC) for the bug and calculated the high percentage of unfixed devices.
Furthermore, the security service website is referring to the CVE-2022-34689 vulnerability. It is a Windows CryptoAPI spoofing vulnerability that allows threat actors to authenticate or sign code as the targeted certificate. As a result, threat actors can use the issue to masquerade as another application or operating system.
What is CVE-2022-34689 vulnerability?
The main cause of the error is the assumption that the MD5-based certificate cache index key is collision-free. MD5’s collision resistance has been known as broken since 2009.
The assault flow is dual. The initial step is to take a legal certificate, change it, and then provide the modified version to the victim. The second process is producing a new certificate whose MD5 collides with the modified legal certificate. Moreover, then utilizing the new certificate to impersonate the subject of the original certificate.
However, there is some good news: CVE-2022-34689 will not be as widely exploited as CVE-2020-0601 also known as “CurveBall”. It is a similar Windows CryptoAPI spoofing vulnerability that has been exploited by Chinese state-sponsored hackers. Once it was one of the top ten most exploited vulnerabilities in 2020.
How do they exploit the vulnerability?
A preimage attack is a process of creating a certificate with an MD5 thumbprint that exactly matches a specified MD5 value. It is computationally impossible even today. However, it is possible to produce two certificates with two different prefixes that have the same MD5 fingerprint. This is known as a selected prefix collision.
If we go this route, we will need to issue two certificates to the victim application. One certificate will be properly signed, validated, and cached (the “updated target certificate”). It will be produced in such a way that it allows a prefix collision attack of your choice. The falsified identity will be contained in the second certificate (which we will refer to as the “malicious certificate”). It will clash with the first certificate’s MD5 thumbprint.
Ignoring the update
Online website security researchers claimed that we discovered almost less than 1% of visible devices in data centers are patched. Thus, leaving the remainder vulnerable to exploitation of this vulnerability.
The researchers verified to The Register that 99% of endpoints were unpatched. However, that doesn’t necessarily imply that they’re susceptible. Yet there still must be a vulnerable app for the attackers to exploit.
The fault was rated with 7.5 severity of “critical” status. Microsoft issued a fix in October 2022, but few customers have yet to use it.
The researchers claimed that so far, they’ve discovered that outdated versions of Chrome and Chromium-based applications are susceptible to abuse. They believe there are more susceptible targets in the wild as the study is ongoing.
Microsoft stated when it first fixed the problem that there was no indication of the vulnerability being abused in the wild. As soon as the Proof of Concept is made public, threat actors will begin looking for weak endpoints. After all, the methodology has already been handed to them; all they need to do now is identify a victim.