Category: Technical
-

Microsoft provides tips on identifying Outlook zero-day exploits
Microsoft released a guide for customers with detection indicators of infiltration by exploiting a recently fixed Outlook zero-day vulnerability. This privilege escalation security gap is in the Outlook client for Windows. It is tracked as CVE-2023-23397, and it allows attackers to obtain NTLM hashes without user intervention in NTLM-relay zero-click attacks. Cybercriminals can use it…
-

Teams: This is what caused the recent massive outage
Teams parent company explains what it believes went wrong. Microsoft Office 365 company has disclosed its first findings about what it believes caused a recent severe outage. This outage affected some of its most popular software services. Users throughout Europe and Asia were unable to use Microsoft 365 services for many hours due to the outage. This…
-

Scam: Bots are opening emails in large numbers!!!
In a scam, bots are involved in opening a significant portion of marketing emails. According to the digital marketing management website Polygraph, a significant proportion around 5% of all marketing emails are opened by bots as scammers flock to “click fraud bots” to falsify email-based conversions. What is Click fraud? Click fraud normally…
-

Web skimming hackers have infiltrated more than 40 e-commerce websites
Experts warn that web skimming assaults are getting more common. Jscrambler, a JavaScript monitoring startup, has found a new set of online skimming attacks, including assaults utilizing methods that are supposedly unidentifiable. The secure website checker organization described how it discovered a web skimming assault on a cheap online marketing and analytics service by registering domain name called Cockpit.…
-

Almost all organizations have adopted Zero Trust Architecture
Businesses are still in the process of migrating to Zero Trust compliance. Most organizations particularly those with a remote or hybrid workforce, are in the process of implementing Zero Trust, but the majority have yet to fully understand the benefits of this relatively new cybersecurity strategy. For its “State of Zero Trust Transformation” report for…
-

Hybrid employees continue to be a huge security concern
According to the research, hybrid employees are still dealing with fraudulent emails. With the majority of company owners finding, it more difficult to guard against cyber threats than before the pandemic, hybrid workers have been blamed for cybersecurity issues during website security audit once again. A cybersecurity website claims employees are the “primary source” of security problems that can…
-

Malware-infested Android apps discovered on Google Play
Over two million individuals have been tricked into installing a new batch of Android malware, phishing, and adware applications that have invaded the Google Play store. Tube Box application Dr. Web antivirus detected the mobile apps, which masquerade as beneficial tools and system optimizers but are the source of performance glitches, advertisements, and user experience…
-

Windows malware searches your phone to exploit data
Malware will also look for any other removable device. Cyber security website experts have uncovered a new malware strain for Windows that is capable of collecting sensitive data from any connected device, including mobile phones, and is reportedly being utilized by North Korean government-linked organizations. The online security website ESET experts claim to have discovered Dolphin, a hitherto undiscovered…
-

Fraudulent Android Applications convert users’ phones into SMS relays
Users may transmit OTP codes to offenders. Researchers have identified a malicious Android-based mobile app that converts smartphones into SMS relays used to validate various online identities. As of now, the app had more than 100,000 downloads on Google Workspace’s parent company app Store and was still available for download. OTPs are Important When people register online accounts, they…
-
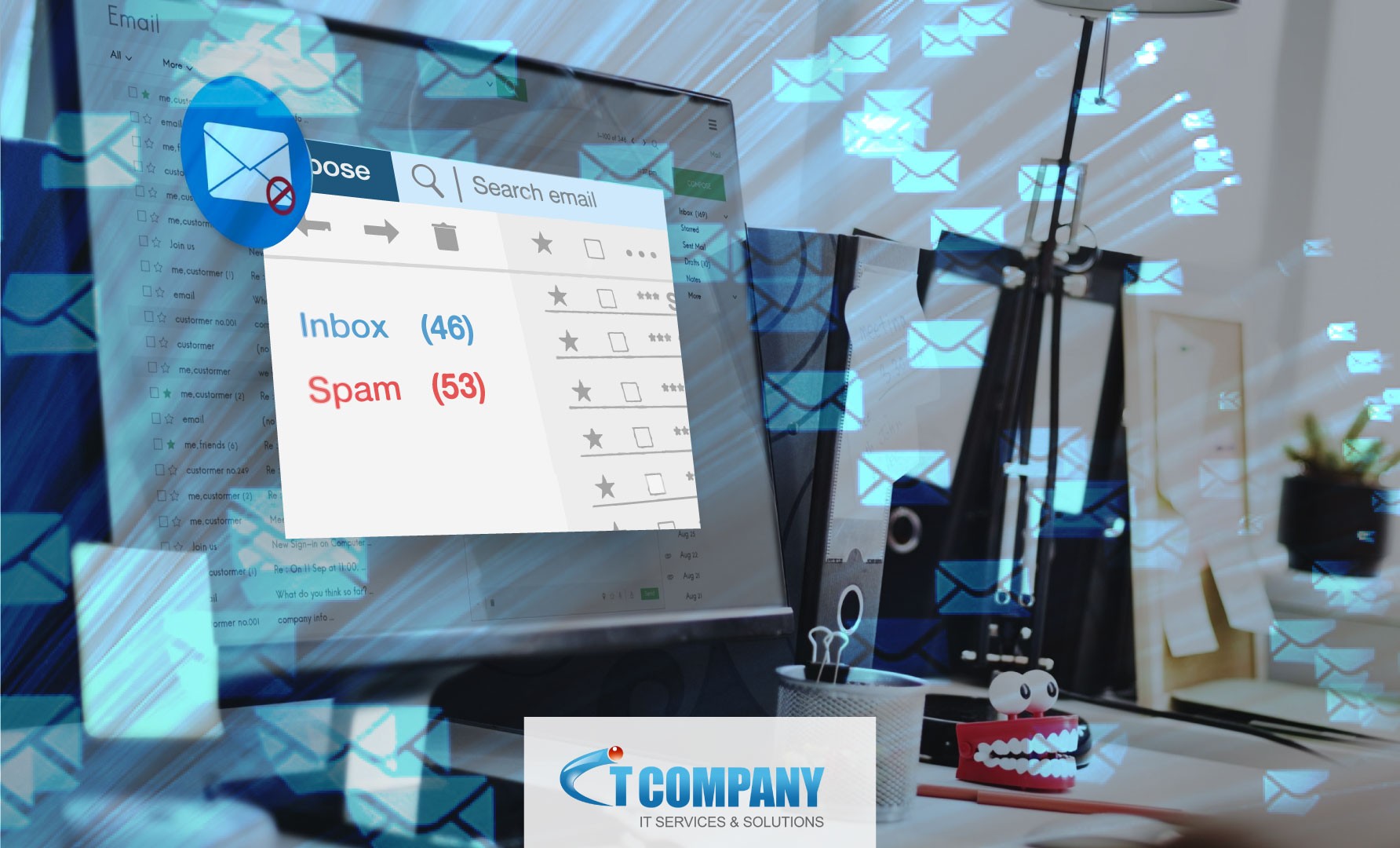
Spam Emails: This could be quite a convenient way to detect them!
Ever wondered what is the most typical spam email subject line? Spam and phishing emails can be harmful since they frequently lead to more destructive cyberattacks. Atlas VPN researchers discovered several common denominators for threat actors delivering spam and phishing emails. The users can utilize this information to detect these emails early and prevent further…
