You may have heard of “PrintNightmare,” a flaw in the Windows Print Spool service that, under some circumstances, might allow hackers to take control of your computer. After raising concerns about the problem last week, Microsoft has now officially released a patch that fixes the problem, and all Windows users are urged to apply it as soon as possible.
We’ll skip the technical details of the patch, but it’s quite simple to set up. However, not everyone may be aware of how to obtain the patch today in order to keep your PC secure when using the Windows Print Spool service to transmit documents from your PC to your printer. With a brief instruction on how to repair the PrintNightmare problem on Windows 10 right now, we’ve got you covered.
As it turns out, several researchers have already identified some more issues with Microsoft’s fast fix, so you’ll probably want to install any future updates Microsoft releases using an approach similar to the one shown below.
Option 1: Visit Windows Update
To begin, go to the Start Menu and then to the left side of your screen to the Settings icon. After that, go to the Windows 10 settings app and choose privacy Update & Security, then Check for Updates. After that, Windows 10 will check for updates.
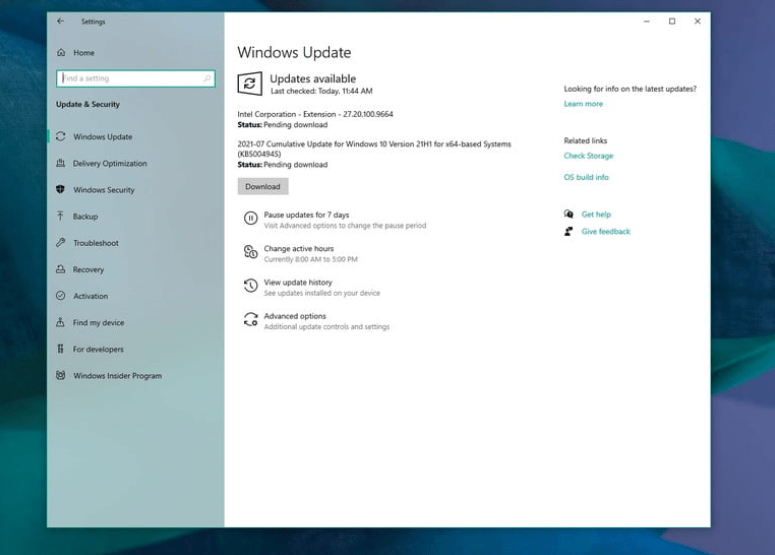
If you’re running the most recent version of Windows, which includes the May 2021 Update (21H1) through the May 2020 Update (20H1), you’ll need to check Windows Update for KB5004945 to cure PrintNightmare. This is the automated patch that resolves the issue in Windows 10 Home, Pro, and other versions of Windows 10.
Allow Windows 10 to download and install the update in the background. After a few moments, the Restart Now button will urge you to restart your computer. Things will be fixed after you resume.
If you’re using an earlier version of Windows 10 (Windows 10 November 2019 Update, also known as 19H2), the patch will be KB5004946. In Windows Update, you should see KB5004949 for all other versions of Windows 10 (Windows 10 April 2018 Update, or version 1803). Your PC will install immediately in all circumstances and will require a fast restart.
Option 2: Download via the Microsoft Update Catalog
In the unlikely event that you don’t see the updates listed above, you can manually download them from the Microsoft Update Catalog. Just be sure to look for the KB version we stated earlier. Where accessible, we’ve additionally listed and linked to these KB versions below for your convenience.
KB5004945 is for all current versions of Windows 10, whereas KB5004946 is for the November 2019 Update for Windows 10. Finally, KB5004949 is for the Windows 10 April 2018 Update, which is version 1803.
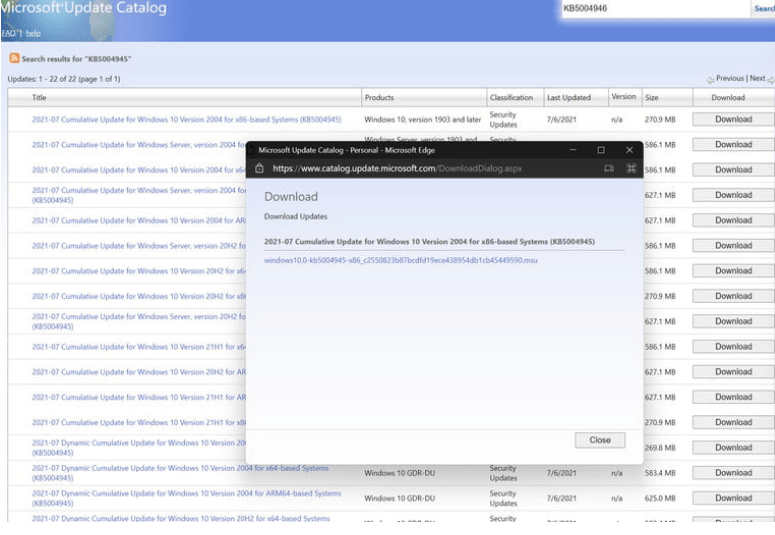
When you click the download button next to these updates in the catalog, a pop-up window will appear. Allow the MSU file to download to your computer by clicking on the link. Once the file has been downloaded, double-click it (straight from the browser window) to have Windows execute and install it. You’ll see that it will look for and install the update. After that, your computer will restart.
On other Windows Versions
If you’re using an earlier version of Windows (such as Windows 8.1 or Windows 7 with extended support), the KB versions will be different. You’ll need to go to Windows Update and check for updates like you normally would. On Windows 8.1, the patch is referred to as KB5004954. Meanwhile, it’s known as KB5004953 on Windows 7.
Again, if you don’t notice these KB updates to patch PrintNightmare, you may manually download and install them from the links we just provided above.
Because Microsoft is labeling all of these KB patches to solve PrintNightmare out-of-band updates (meaning they aren’t part of the usual schedule), they should install immediately and appear on your PC without any action on your part.